Complete Visibility,
Optimum Cybersecurity
Unique technology and an expert 24x7 SOC address today’s most critical security questions.
Why UncommonX
MDR/XDR PLATFORM
Our SaaS Platform empowers teams across organizations of all sizes to maximize the return on existing IT investments by providing a single integration point for ingesting, aggregating and correlating your enterprise security, IT and business data. It processes information directly from your installed solutions against a standardized set of metrics and best practices to produce an intelligent, real-time assessment of your cyber risk.
+
24/7/365 SOC
The UncommonX SOC protects your organization from external threats and manages remediation 24/7, 365 days a year. Our SOC leverages the power of the UncommonX platform and its unique integration hub that deploys faster and easier than any other solution. We integrate with customer ticketing systems and perform full-service containment through remediation. Our SOC acts as a seamless extension of your team.
UncommonX Solutions

UncommonX MDR/XDR
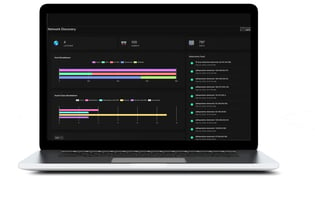
Agentless discovery provides complete visibility to all of your system elements and security gaps.

24/7 Managed SOC
Protects your organization from external threats and manages remediation, 24/7, 365 days a year.

Asset Discovery and Management
Know exactly what devices and systems are in place, and manage your business more effectively.

Vulnerability Management
Progressively manage your security and IT strategy, adjusting key policies based on threat intelligence.

XDR for Managed Service Providers
Intelligent and scalable solution to enhance value for your SMB and enterprise customer relationships.

MDR for Education
The UncommonX MDR solution provides enterprise scale security solutions for school districts of all sizes.
Enabling Customer Success
"UncommonX was the only MDR vendor able to provide us with such a detailed, comprehensive view of our entire network. They uncovered and delivered the critical insight needed to help our city improve its cyber security posture in days."
- Lloyd Keith, CIO for the City of Gary, Indiana
Why Cyber Intelligence Is Critical for Cybersecurity
UncommonX Founder and Chief Innovation Officer Ray Hicks defines cyber intelligence, how it works, and why it and predicative modeling are critical components of effective cybersecurity.
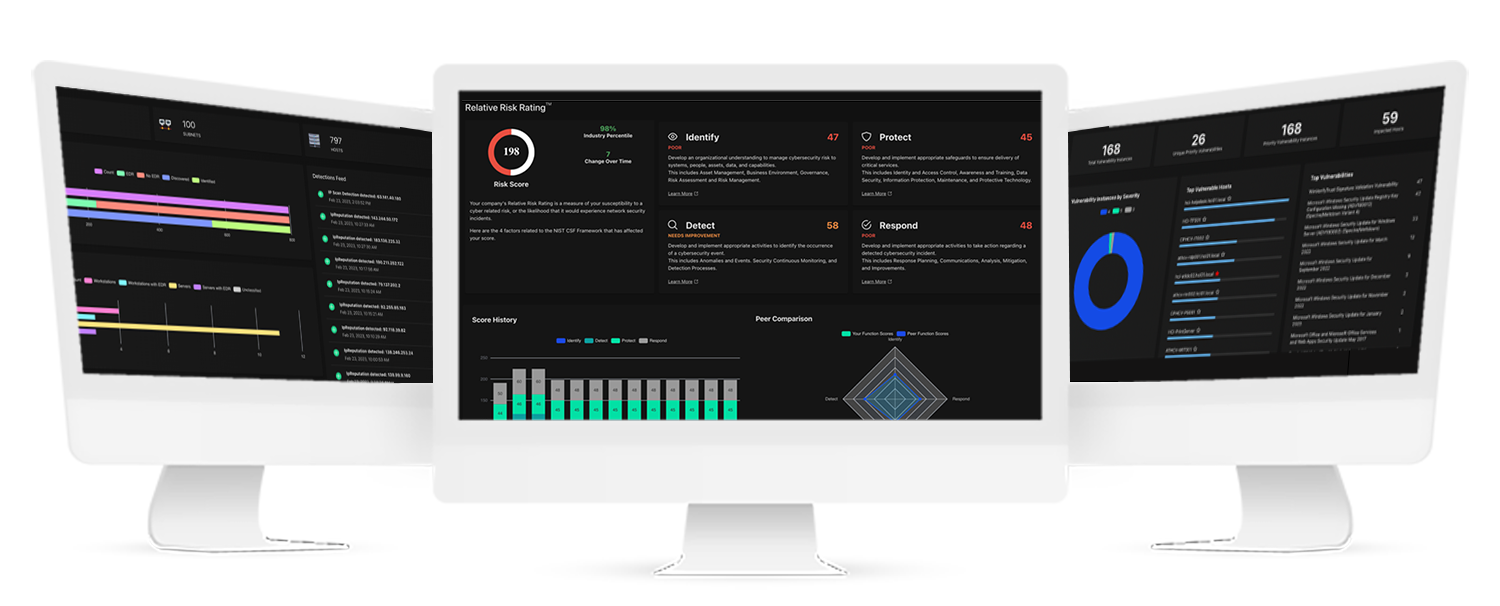
Intuitive Visualizations For Fast Decisions and Robust Reporting
Agentless Discovery of all network elements, analysis of traffic and trends, and deep dives on any specific device, app, host, iOT/OT, or cloud service.
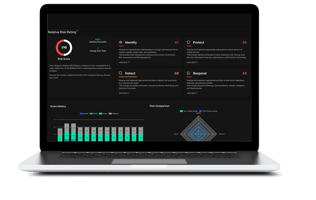
Relative Risk Rating (R3) across standard NIST risk factors for your entire environment with intelligent insights on risks and resources.
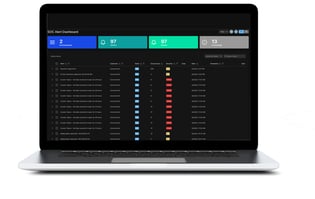
Real-time alert dashboard sorts and prioritizes from all connected devices and helps investigate, contain, and remediate.
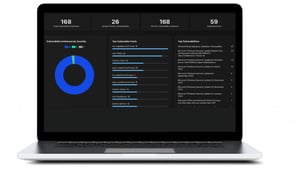
Central Intelligence feature provides comprehensive assessment of vulnerabilities and enables proactive threat hunting.